Page 2 of 2
Posted: Mon Feb 12, 2007 9:35 pm
by ob1
Oh my god !!!!
It's foggy, but how fast !!!
I'm still very modest : I don't have any clue about texturing. I'd go for flat shading first, then Gouraud, then .... Well, let's start with the very beggining !!!
Posted: Tue Feb 13, 2007 6:30 am
by TmEE co.(TM)
ob1 wrote:I won't swap my barrel of Charles Doty's ASM with 2 barrels of SNASM !!!

Anyway, SNASM doesn't run @ work (where 95% of my GEnesis job is done

)
Maybe you should get XP compatible SNASM ?
Posted: Tue Feb 13, 2007 7:51 am
by ob1
I have Win 2000.
Where can I get one ? And SNASMSH by the way.
Posted: Tue Feb 13, 2007 8:47 am
by Ketsuban
SNASM68K for XP can be found at
drx's site. SNASMSH2 can be found at
Bart Trzynadlowski's site.
For purely 68k work, however, I recommend
AS.
Posted: Tue Feb 13, 2007 1:24 pm
by TmEE co.(TM)
ob1 wrote:I have Win 2000.
Where can I get one ? And SNASMSH by the way.
XP and 2K are practically same, XP just has little better 9x/DOS support and is not as jerky as 2K (In my experience 2K is not much better than ME).
I got SNASMSH2 from a 32x dev thing I downloaded somewhere... Can't remember. 2K/XP SNASM68K is available at Devster's site
Posted: Tue Jul 03, 2007 2:30 am
by cdoty
ob1 wrote:Anyway, SNASM doesn't run @ work (where 95% of my GEnesis job is done

)
There's a version on Devster's site that runs fine on WinXP (and probably Win2k).
Another option is GNU 'as'. The only changes are comments and hex numbers.
Posted: Tue Jul 03, 2007 11:35 am
by TmEE co.(TM)
BTW, the XP version runs flawlessly on my Win98SE machine.
Re: 32x "security code" reverse engineered
Posted: Tue Feb 23, 2021 1:43 pm
by ob1
Sorry to relive a topic - again !,
but there is one line of code that I find surprising.
Just between SDER and TV Mode Check, we have
Code: Select all
move.l #$8802A2,$70 ; 21 FC 00 88 02 A2 00 70
If my 68k isn't too rusty, I translate this by
"write the value 0x8802a2 ... in ROM ?!"
First of all, how is it possible to write in ROM ?
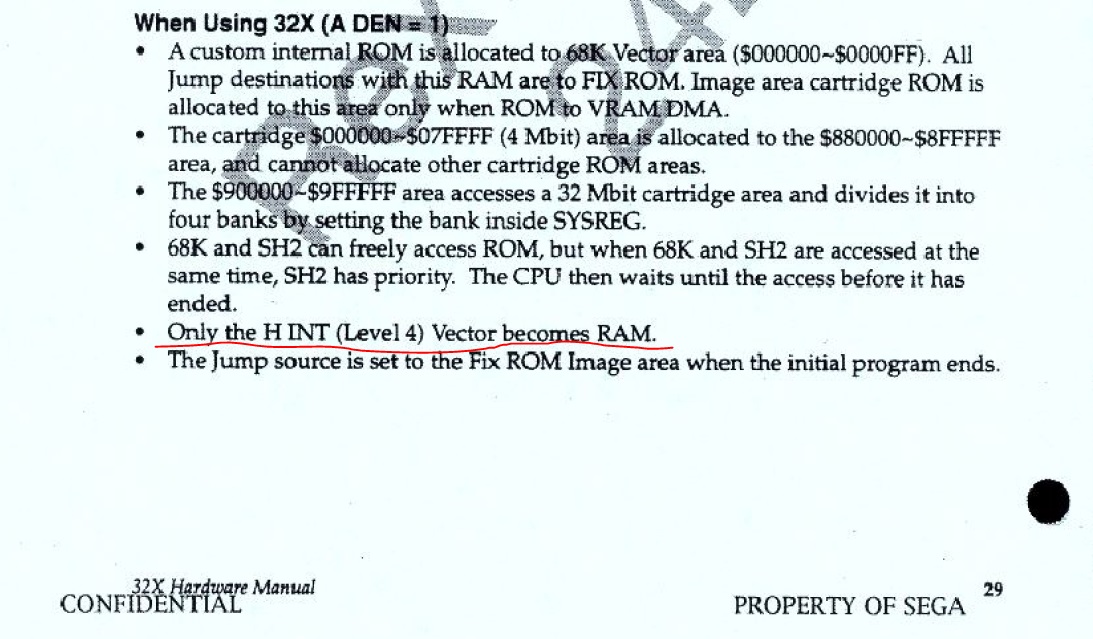
Secondly, 0x70 is the offset for the Level 4 Interrupt (H INT), and 0x2a2 is the offset of the level 4 interrupt once the memory map was changed by setting ADEN. But what would be the point of copying this address ?
Re: 32x "security code" reverse engineered
Posted: Tue Feb 23, 2021 3:03 pm
by srg320
From 32X Overview, the same as in Sega CD.
- Снимок.jpg (190.73 KiB) Viewed 15891 times
Re: 32x "security code" reverse engineered
Posted: Tue Feb 23, 2021 3:51 pm
by ob1
Hello @srg320, and thank you very much for you quick answer.
Are you telling me that the custom internal ROM ($00~$FF) is actually ... RAM ?
Re: 32x "security code" reverse engineered
Posted: Tue Feb 23, 2021 4:06 pm
by srg320
No, just area 0x70-0x73. Maybe it's a separate register.
The same register is in Sega СD and some games change it as needed.
Re: 32x "security code" reverse engineered
Posted: Tue Feb 23, 2021 4:56 pm
by ob1
OK I got it.
Quite new for me, but that explains a lot.
Thank you very much ^^
Re: 32x "security code" reverse engineered
Posted: Wed Dec 08, 2021 7:38 am
by ob1
So,I've done my homework, and indeed, I can write at 0x70!!
Tested on Fusion and real (PAL) hardware.
Unfortunately, it looks like it doesn't work on Gens.
I can write 0x70, the KMod debug window tells me it has been modified,
but when H_INT happens, it looks like it goes to 8802A2 no matter what.

- gens.png (15.1 KiB) Viewed 13453 times
May need to try a bit more on this point.